
Computer Viruses
 Content of the lesson:
Content of the lesson:
- Computer Virus
- Basic Forms
- Special Cases
Computer Virus in General
You can also use another term for a computer virus - Malware = Malign Software = harmful software.
It is a computer program which is distributed without the consciousness of a user and its task is to damage a computer. Every computer virus can be defined in this way.
Why is harmful software called as a virus? Because of the similarity with biological viruses. Computer viruses also spread quietly, reproduce other viruses and move them to other computers.
Signs of Computer Viruses
We can take a look at often signs of computer viruses. These signs do not have to mean that a computer was attacked, usually more signs are combined. However, it can be a small technical fault of a computer.
- Blocking space - Virus is also a program and needs to be stored inside computer. It can be stored on a hard drive or inside the operating memory. Blocked space is minimal but it exists.
- Slowdown of system - Virus can cause slowdown of the whole system. It also needs system resources besides the space so it uses computer components as any other program.
- Unstable system - Viruses are not developed as other applications and not tested on different configurations and platforms. This can cause problems with stability of system. Your programs can crash or the whole system can remain without response.
- Graphical and sound elements - Various nonsenses like title on monitor, replaced letters in text, beeping or whistling. A good example is the Ambulance virus - an ambulance was driving on your screen and was making loud sounds of a siren.
- Data stealing - New viruses are designed to steal data. This procedure is usually done via e-mails because the virus is set to send data from your computer to a concrete or a random person.
- Data encryption - Also an often sign of a computer virus. After attacking a computer it encrypts data on your hard drive and displays a warning that you should pay money to an account. This virus takes your data as its hostage and threatens that it will be deleted in case you do not pay.
- Data destruction - The worst variant for computer users. The virus does not ask you and deletes data on the hard drive. This can happen in a short while or slowly and quietly. This is a malignity, nothing else.
General Procedure of a Virus
- taking control over the processor
- checking the current state of environment
- installing into memory
- forwarding interruption (IRQ)
- test on the condition of launching damage (date, number of launches)
- making the damaging activity
- finding a place for creating copies
- checking the place whether it already contains a copy or not
- inserting copy
- encrypting attacked place
Note: the order is individual; all actions do not have to be done
Parts of a Computer Virus
- reproduction part – this is the main part of a computer virus, its primary task is to ensure further distribution
Other parts are not compulsory:
- analytical part – this part checks your computer and finds out the following facts :
- availability of antivirus programs - virus will try to deactivate or fool the antivirus program not to be revealed
- unprotected network for further distribution
- action part – this part is designed for manipulations with data, for example for its destruction
- launching mechanism – several viruses can behave normally until a particular moment - they wait for their opportunity, for example a concrete day, hour, opening a file for the x-time (an example is the CIH (Černobyl) virus which was launched on 26.4.)
- masking part – this part tries to mask the virus to be kept in secret - it modifies its appearance, encrypts it, copies it to unusual places (help, HTML documents)
Basic Forms
Viruses
Classical viruses are rather a history. We will not deal with them in details, we will make a short summary.
A classical computer virus attacked a concrete program of file where it settled and masked itself. It attacked executable files, system areas of disks or files which cannot be created straight but only using specific applications (Word documents, Visual Basic scripts etc.). The virus was then activated after launching the file because the file also launched the virus.
- Types of viruses - according to attacked objects
- Bootviruses - They attack only system areas (partition table, boot sector of a hard drive or diskettes in the past). It was activated after launching a computer when the operating system from the attacked disk was booted. In case that you forget an infected diskette inside drive, it was booted before the operating system and the virus was loaded.
- File viruses - As the name says, they attack files
(for example EXE). Using an attacked file means activating the virus.
- Overwriting virus - It damages the previous file because it overwrites it with a new content. The previous file is not usable because the virus is hidden inside it. This variant is quite noticeable. These viruses sometimes tried to mask themselves using an error warning.
- Link virus (parasitic) - More intelligent way of infection when the virus was added to an existing file. When such a file was opened, the virus was usually launched at first and then the file behaved normally.
- Accompanying virus - Very old variant. This virus used properties of old operating systems when a copy of executable files was saved with the extension COM. System then launched this extension at first. The virus was launched at first and then the program started normally.
- Multiparital - This type attacks files and system areas at once. It combines advantages of both ways. This type is loaded to memory from the system area and then waits until the operating system is fully loaded. Then it can take control of the "higher level" services of system. An example is One_Half – one of the most spread multiparital viruses in the world.
- Macroviruses - The target of these viruses are office packages which supports macros (programs written in a programming language). Macros are part of the office software; an example is Visual Basic in MS Office. Famous target is the scheme normal.dot because then the virus is copied inside every new file. Because of this, you can get warning message when opening several documents which asks you if the macros should be allowed. This is because you downloaded the file from an untrustworthy source and you risk being attacked.
- Types of viruses - special properties
- virus of straight action (non-resident) - one action is done when the virus does everything it wanted and then it is closed
- resident virus - it hides inside the operating memory and observes the currently launched applications and files. Then it attacks these files.
- Stealth (secret) virus - one of its parts is an intelligent tool for fooling antivirus programs, the virus tries to mask and hide itself - it saves the previous state of operating memory and gives it to antivirus software in case the memory is checked.
- fast infector - this is a resident virus which is spread very fast, attackes everything but also gets much more attention than the other viruses
- slow infector - this virus spreads slowly so it cannot be revealed for example with the integrity test (comparison of changes in a time horizont)
- polymorphous virus - it tries to change very often and uses different functions so when an antivirus searches for its common features, it might not reveal it
Trojan Horses
The name of this harmful software is derived from mythology. We all know the story how Greeks broke to Troy using a trick with huge wooden horse. When Trojans saw that the Greeks were leaving, they ran out of their city and found a massive wooden horse and one Greek who told them that it is a gift for goddess Athena. The horse was so huge that it did not fit into the gate so Trojans destroyed part of walls and moved the horse inside the city. When the night came, Greek ships returned to shores of Troy and gave a sign on the ground. Hidden Greeks ran out of the horse and together with the others from ships captured Troy.
A computer Trojan horse uses the same principle - it uses human curiosity and stupidity. Users are easily tempted to open a program of a file. Trojan horses do not distribute themselves as other classical viruses. The only way how to heal your computer is to delete all Trojan horses hidden in files.
- Password-stealing Trojan (PWS) - Very dangerous Trojan horse which monitors all usernames and passwords. These are saved and sent to a particular place. Sensitive details like usernames for bank accounts can be stolen using this way.
- Destructive Trojans - They destruct your data. Delete, rewrite, encrypt. Or the virus can easily format your disk.
- Backdoor - This means an unauthorized access to a
computer. If you use for example RealVNC, you know that this program
runs as a server on one computer and as a client on another one. The
client can connect to the server anytime. In case of RealVNC you need a
special browser for this, IP address and usually a password. A Trojan
horse called Backdoor does the same. The only difference is that the
user does not know about this and has no possibility to find it out.
- IRC - Special group for communication using a channel in IRC network. A person who controls the Trojan horse can control all computers of such a network by control commands.
- Dropper - Once you run such a Trojan horse, it will extract many other viruses which are hidden inside it.
- Downloader (TrojanDownloader) - Additional viruses and Trojan horses are downloaded from the Internet after launching it. You can run it without noticing this. While surfing on the Internet, it is accidentally saved and launched. It usually uses security holds of your system or used program.
- ProxyTrojan (TrojanProxy) - Unpleasant Trojan Horse which can get your organization into so called black list - a list of spam (unwanted mail) distributors. It settles in a computer, connects to a SMTP server and starts sending large amount of e-mails from your computer.
Worms
- Email worm - Its task is to reapply and distribute itself and it uses computer users for this purpose. It starts sending e-mails with infected attachment. In case it gets to a computer, it can make large amount of copies and start sending them. It will send them to all your contacts inside your e-mail client. This causes the network to be overloaded. In case that it sends emails to more people, it will cause them similar problems. This can lead to an avalanche effect.
- Network worm - This type of worm is fully independent. It does not need anybody or anything. It uses security holes in systems and in network programs. The term worm was firstly used for so called Morris worm. This worm in 1989 overloaded a large part of network which was the predecessor of the Internet. This harmful worm works on a lower network level then the other ones. It does not send infected files but infected packets. Sending these packets is random or uses a concrete scheme. Antivirus programs usually cannot catch this type of malware before it is activated but in this moment the computer is already infected. Because of this you have to actualize your system and all used programs to prevent security holes which can let this worm to get into your computer.
Special Cases
Spyware
Spyware is not a thread but rather an inconvenience. It sends data from your computer but this data is used for statistics only. It can find out the number of visited websites, number and type of installed programs etc. Unfortunately, this information is being misused for targeted advertisement which should be attractive for the concrete user. Spyware is fully legal so far and is often a part of program examples. However, it is still a malware which runs without the consciousness of user and can cause slowdown of programs or the whole system.
Adware
This group contains programs which contain advertisement. User usually agrees with this when installing such a program. However, Adware can also bring pop-up advertising windows when browsing the Internet. It also forces you to change your default pages for browsers etc. In most cases you are not interested in that website at all.
Hoax
An interesting variant of harmful software. In fact, it is not harmful software but only a false message, journalism duck or nonsense. Such a message should alarm users. Usually used topics are connected with dangers for example a threat of an attack which can cause your hard drive to rotate in the other direction and explode. Then you can get warnings from organizations, false help requests, fraudulent emails (mostly from Niger) and more. One of the most known hoax is the message that the Mars will be visible at night sky as well as the Moon because it is closer to the Earth and this situation can be seen once in many years. This message has been sent around the Internet for many years and several people still believe it.
More about hoax: www.hoax.cz
Dailer
A thing from the past. It was used when the internet connection used a fixed line. This Trojan horse forwarded your call for example to so called yellow pages where the price for loading a page was not 1 Kč, but 60 Kč for example. You could get this virus when visiting a pornographic website or because of a security hole in your browser. Favorite technology of this virus was the element ActiveX.
Phishing
A typical example is that you get an e-mail which contains all requirements of your bank (logo, colors, appearance). There is a message telling you about a regular maintenance and you will be prompted to send your username, password and sometimes also the pin. Otherwise your account will be blocked or removed. You fill everything, click on the link and send data... and you have just sent your account details to a foreign person. Even though the website looked like the website of your bank. As you probably suspect at this moment, these e-mails are fraudulent and try to get sensitive information from you - this procedure is called social engineering.
Pharming
It is closely connected to phishing and is even more insidious. The difference is that an owner of a bank account enters the address "www.mojebanka.cz" into his browser, enters the right category and logs in to his account. The procedure is fully correct but the attacker changed so called DNS record. This means that you enter the address www.mojebanka.cz and a DNS server translates the IP address of that computer and redirects you to that machine. However, it can happen that DNS records were changed and you will be redirected to another IP address - a pre-prepared one which contains the same appearance of website as the real bank. Because of this reason banks usually require a combined way of logging in and confirming payments. This means that you log into your account using the right username and password but you also have to enter a certificate which was sent to your mobile phone. This can prevent your account to be misused.
Examples of Viruses
Brain
Year 1986. The first virus (boot virus). It was designed for system MS-DOS. It was not meant to damage computers but it was designed as a protection (advertisement) against copying a medical program which was created by brothers Alvi in Pakistan. Virus was not destructive, only contained contact details but these made the life of many users unpleasant.

Virus Brian (source: www.lupa.cz)
Christmas Tree
Year 1987. This was the first network epidemic. Virus displayed an image of Christmas tree and also sent his copies to all network users. It was spread inside university networks, concretely the Bitnet network in western Germany from which it spread to European academic institute and then to IBM. This virus was followed by more viruses (Jerusalem and Morris).

Virus Christmas Tree (source: nakedsecurity.sophos.com)
Morris Worm
Year 1988. Morris worm, sometimes also called as the Internet worm, was one of the first worms which used the Internet to spread. His author was Robert Tappan Morris who created it in 23 at university in Cornelloě during his scientific work. This worm worked on systems based on Unix. When experimenting with this program it started spreading in the whole network and attacking other computers without control. The original intention was not to damage anything but to find out the number of users connected to the Internet. However, the virus contained a mistake which allowed it to attack one computer more times and then this machine was damaged so much that working on it was not possible.
Moris was the first person who was accused of violating the law. He was released on a condition and had to work several hours in the streets. Nowadays this author is an associate professor at the Massachussest Institute of Technology where he focuses on computer networks and their security.
Michelangelo
Year 1992. This virus caused especially a huge media buzz. It waited for the date 6. March inside all computers - this is the birthday of the artist Michelangelo - and then it rewrote a part of hard drive using random characters. There were worries that data in millions of computers were destroyed but this was a clever move of antivirus companies which earned money for their programs. The real number of infected computers was around 10-20 thousand.
One Half
This is one half.
Press any key to continue...
Year 1994. This virus came from Slovakia and was also called as "plague from Košice". It could completely modify his copies what made the process of revealing it very difficult (that means it was a polymorphous virus). It infected executable files with extensions .exe and .com (while launching, opening, renaming) but also the boot sector (that means it was a hybrid virus) and managed to hide his presence in a computer (it used stealth techniques).
It was a destructive virus which encrypted a part of your hard drive. In case that you remove the virus, you lose the encryption key. To prevent the loss of data, you have to leave the virus inside a computer and backup everything on another medium. There was also a program which was able to decrypt the data because the virus saved his encryption key inside the partition table.
Chernobyl
Year 1998. The real name was Win95.CIH. Virus was created by a Taiwan programmer Chen Ing-Hau (CIH) who sent it to a local conference. This virus is activated every year on the anniversary of nuclear plant fault in Chernobyl - on the 26. April. It was designed for Windows 95 and Windows 98. It was insidious because it could delete Flash BIOS which meant destruction of the whole motherboard in several cases. This means it was able to damage the hardware of a computer.
Mellisa
Year 2000. This was a macrovirus which used programs from Microsoft (Word, Outlook). It was spread very quickly using the Internet, users got an e-mail with attached file "List.doc". After opening this file the virus was launched. Then it sent itself to first 50 contacts saved in Outlook. Gradually all other Word documents inside the computer were infected. The author was finally traced by FBI.
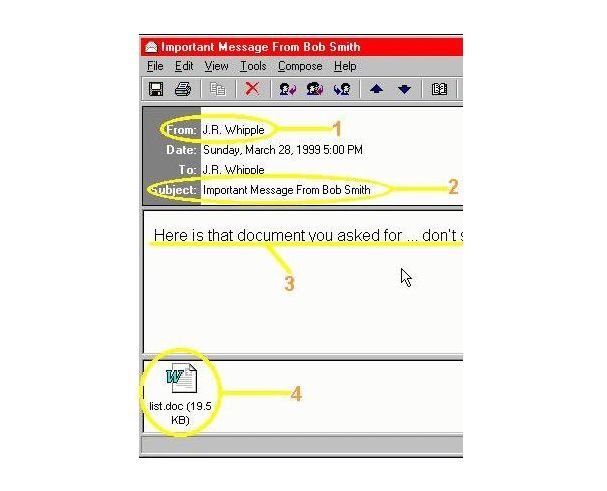
Virus Mellisa (source: tn.nova.cz)
I Love You (Loveletter)
May 2000. This was a famous e-mail worm created in Visual Basic. It was released on 4. May 2000 on Philippines and is considered as one of the most destructive viruses. It simply sent an e-mail with infected attachment. The whole email looked correctly and there was one file attached to the email ("love-letter-for-you.txt"). User who thought that it is a text file opened the attachment and launched the virus. The real name was: "love-letter-for-you.txt.vbs". The operating system hides extensions of known files so this attachment looked like a simple text file. We can use the term "social engineering" with means manipulating with people for this virus. The target is to force people to do a particular action or to get information from them.

Virus I Love You (source: www.f-secure.com)
Anna Kurnikovova
Year 2001. Quickly spreading virus, it was not destructive. This virus was generated using a virus generator. Users got an image named anna-kournikova.jpg in an e-mail (the real name was anna-kournikova.jpg.vbs of course). User was lured to open a photo of the famous tennis player and launched the virus after opening the file. Then this virus was sent to all his contacts.
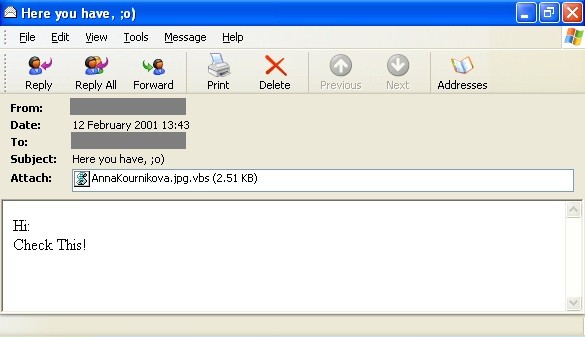
Virus Anna Kurnikovova (source: www.cnews.cz)
Code Red
July 2001. Example of the strength of worms. During 14 hours more than 359 000 computers using randomly selected IP addresses were infected. It was not destructive, did not steal any data or modify anything. It attacked Microsoft IIS web server and displayed the following message: "HELLO! Welcome to http://www.worm.com! Hacked By Chinese!". His spread stopped at midnight because it was programmed to do so. Users could remove it by restart and then had to patch the vulnerable place.

Virus Code Red (source: www.pooh.cz)
Blaster (Lovsan)
Year 2003. Widespread virus which used a security hole in Microsoft systems. It was not destructive, only pointed on weak parts of systems Windows 2000 and Windows XP. User got a warning message (see the following image) and then his computer was restarted. The virus probably also contained a message to Bill Gates that he only earns money but cannot secure his own software.

Virus Blaster (source: www.viry.cz)
Sasser
This virus used a security hole (Local Security Authority Subsystem Service) to display a warning and then restarted the computer.

Virus Sasser (source: www.viry.cz)

Virus Sasser (source: www.viry.cz)
My Doom (Novarg, Shimgapi)
Year 2004. This virus was spread using e-mails and lured users to open an infected attachment. It was a so called backdoor which opened ports for remote access into a computer. The attacker could take control over any infected computer.
Storm Worm
Year 2007. This virus also used e-mails to spread and lured users to open an infected attachment. In case that someone opened it, his computer was infected. This virus masked itself using a rootkit which hid his presence in a computer. Then it took control over the computer and connected to peer-to-peer network (this virus managed to use one of the largest networks in the world to connect computers). Then it sent copies to other computers of course. This virus was very variable, there were several variants, it changed his programming techniques, methods of infection and procedures of social engineering.
Additional Texts
Questions
- Characterize a computer virus.
- What is a Trojan horse? Name several examples and characteristics.
- Which types of computer worms do you know?
- What is HOAX and what is its purpose?
- What is the difference between phishing and pharming?